Order Number: AA-PGBXD-TE
This guide describes the POLYCENTER Security Compliance Manager for OpenVMS product and provides information on its use.
Revision Information: This manual has been revised for V3.1.
Operating System: OpenVMS Alpha or OpenVMS VAX Version 6.2 or higher.
Software Version: POLYCENTER Security Compliance Manager for OpenVMS, Version 3.1
The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document.
Possession, use, dissemination, or duplication of the software described in this documentation is authorized only pursuant to a valid written license from Digital or the third-party owner of the software copyright.
No responsibility is assumed for the use or reliability of software or equipment that is not supplied by Digital Equipment Corporation.
Digital Equipment Corporation makes no representations that the interconnection of its products in the manner described in this document will not infringe existing or future patent rights, nor do the descriptions contained in this document imply the granting of licenses to make, use, or sell equipment or software in accordance with the description.
The product described in this document is intended to assist customers in maintaining an appropriately secure systems environment when used in conjunction with customers' vigilant operational security practices. Digital does not guarantee or warrant that the use of this product will provide complete security protection for customers' systems.
The following are trademarks of Digital Equipment Corporation: AXP, DEC, DECinspect, DECnet, DEC SecurityGate, Digital, OpenVMS, POLYCENTER, ULTRIX, VAX, and the DIGITAL logo.
Microsoft and Windows are registered trademarks of Microsoft Corporation.
Motif is a registered trademark of the Open Software Foundation, Inc.
UNIX is a registered trademark in the United States and other countries, licensed exclusively through X/Open Company Ltd.
All other trademarks and registered trademarks are the property of their respective holders.
| Contents | Index |
This guide describes POLYCENTERtm Security Compliance Manager (POLYCENTER Security CM) for OpenVMStm and provides information to help you to use it effectively.
POLYCENTER Security CM is a software product that you can use to automate the implementation of your security policy.
This guide is intended for system administrators, and others who are responsible for system security.
The following documents contains more information about POLYCENTER Security CM:
POLYCENTER Security Compliance Manager for OpenVMS Installation Guide --- This document describes how to install POLYCENTER Security CM on OpenVMS Alpha and OpenVMS VAX systems.
POLYCENTER Security Console for Microsoft Windows Installation and User's Guide --- This document describes POLYCENTER Security Console, a PC tool that you can use to manage POLYCENTER Security CM on a group of nodes. It provides information on its use.
This guide is organized as follows:
| Chapter | Title | Contents |
|---|---|---|
| 1 | Overview of POLYCENTER Security CM | Gives an overview of POLYCENTER Security CM and how you can use it to improve the security of computer systems. |
| 2 | User-Defined Tests | Describes how to create your own test collections. |
| 3 | The Command Line Interface | Describes how to carry out POLYCENTER Security CM tasks using the command line interface. |
| A | Distributing Inspectors | Describes how to use a sample inspector to implement your security policy and how to distribute the inspector. |
| B | Troubleshooting | Describes troubleshooting techniques and typical problems and solutions. |
| C | Tokens | Provides information about tokens generated by POLYCENTER Security CM. |
The following conventions are used in this guide:
| Convention | Description |
|---|---|
| Note | A note contains information that is of special importance to the reader. |
| Caution | A caution contains information to prevent damage to the equipment. |
| Monospace type | Monospace type indicates system displays and user input. It also indicates keywords and literal strings in text. |
| Boldface type | Boldface type in text indicates the first instance of terms defined in the text, in the glossary, or both. |
| italic type | Italic type indicates variables and indicates the complete titles of manuals. |
| Ctrl/ X | Ctrl/ X indicates that you hold down the Ctrl key while you press another key (indicated here by X). |
| [ ] | In format descriptions, brackets indicate optional elements. You can choose none, one, or all of the options. |
| nn nnn.nnn nn | A space character separates digits in numerals with 5 or more digits. For example, 10 000 equals ten thousand. |
| n.nn | A period in numerals signals the decimal point indicator. For example, 1.75 equals one and three-fourths. |
This chapter gives an overview of POLYCENTER Security CM and explains how you can use it to enhance the security of computer systems.
This chapter contains the following sections:
1.1 Enhancing the Security of Computer Systems
The ability to protect the integrity of confidential data and programs is vital in every enterprise. Distributed computing and an increased reliance on computer networks present a possible threat to the security of computer systems. A computer must be secure enough to withstand attacks from external unauthorized parties and to protect users from accidental or malicious actions of other users.
POLYCENTER Security CM allows you to monitor and analyze operating system and network settings periodically to ensure that they comply with your organization's security standards. You can use POLYCENTER Security CM to design and implement your organization's security policy. You use the POLYCENTER Security CM tests as building blocks to do this task.
POLYCENTER Security CM is a member of the POLYCENTER family of security products. Other security products in the POLYCENTER family include:
1.2 Components of POLYCENTER Security CM
This section describes the components of POLYCENTER Security CM and the output that it produces.
POLYCENTER Security CM comprises the following main components:
The following diagram shows the components of POLYCENTER Security CM and how it interacts with POLYCENTER Security Console:
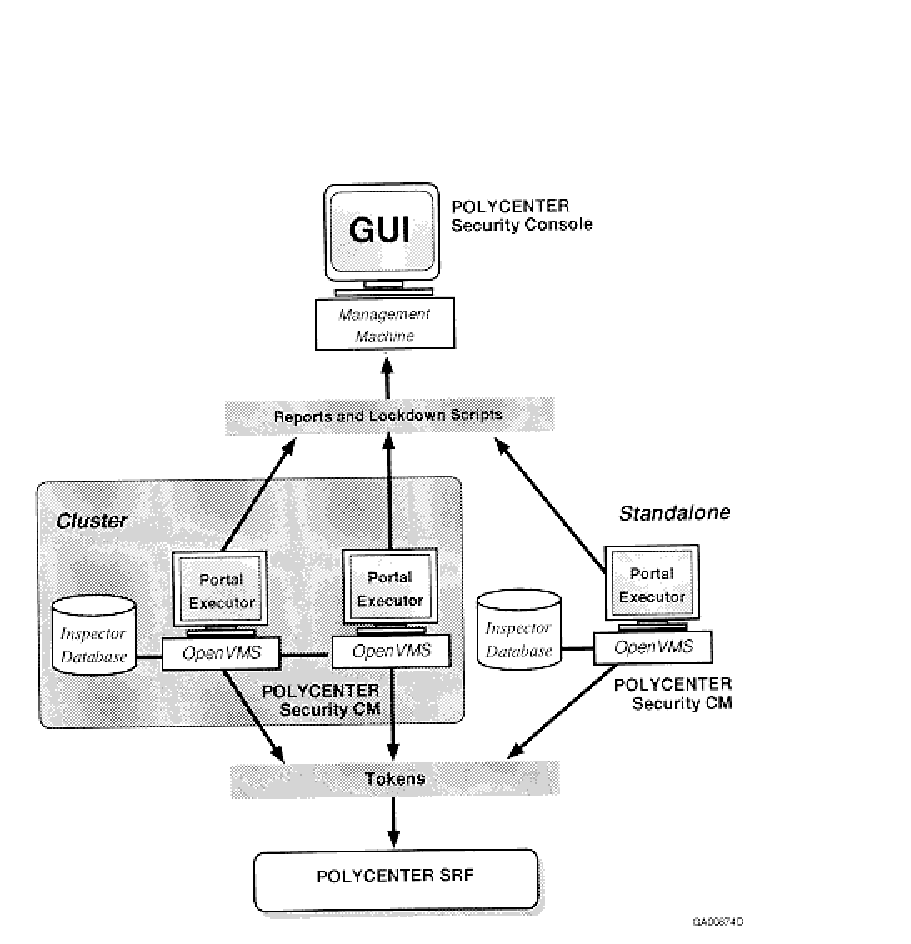
POLYCENTER Security CM can produce the following output:
1.3 POLYCENTER Security CM Tests
POLYCENTER Security CM stores its tests in a hierarchical structure. This section describes the test hierarchy and the available subsystems.
The following table describes the elements of the test hierarchy:
| Element | Description |
|---|---|
| Inspector | The object that POLYCENTER Security CM uses to hold tests and related information needed to test the system's security settings. |
| Subsystem | A category of related system settings to be tested, for example, accounts. |
| Test Collection | A subcategory of the related system settings. This is represented on the POLYCENTER Security Console GUI as a test dialog in which you can specify values. |
The following table provides a summary description of the available subsystems. See the POLYCENTER Security Console GUI online help for detailed information on subsystems and tests.
| Subsystem | Description |
|---|---|
| Auditing | Allows you to check that security auditing and accounting are implemented correctly on your system. It also allows you to check that the AUDIT_SERVER process and the OPCOM process are running. |
| SYSGEN | Allows you to check that settings for system parameters related to system security are secure. |
| Accounts | Allows you to check that accounts on your system are secure. |
| Files | Allows you to check that files on your system are secure. You can specify which file protection, UIC, and ACL are required for each file. |
| Passwords | Allows you to check that password security is enforced on your systems. |
| Network | Allows you to check DECnet proxies and banner messages displayed on your system. |
| Miscellaneous | Allows you to include your own programs. |
1.4 New Features in Version 3.1
Version 3.1 is a maintenance release of POLYCENTER Security CM V3.0. New date formats have been changed to 4-digit years to insure Y2K compliance.
1.5 Getting Help and More Information
This section describes where to find more information to help you to use POLYCENTER Security CM.
The POLYCENTER Security Console GUI includes a tutorial. The tutorial is accessible from the Help menu.
Detailed help on all aspects of POLYCENTER Security CM is available from the POLYCENTER Security Console GUI on the PC. The help includes information on the following:
See the POLYCENTER Security Console for Microsoft Windows NT 4.0 Installation and User's Guide for more information.
| Next | Contents | Index |